Malware analysis Malicious activity
Por um escritor misterioso
Descrição

Security Orchestration Use Case: Automating Malware Analysis - Palo Alto Networks Blog
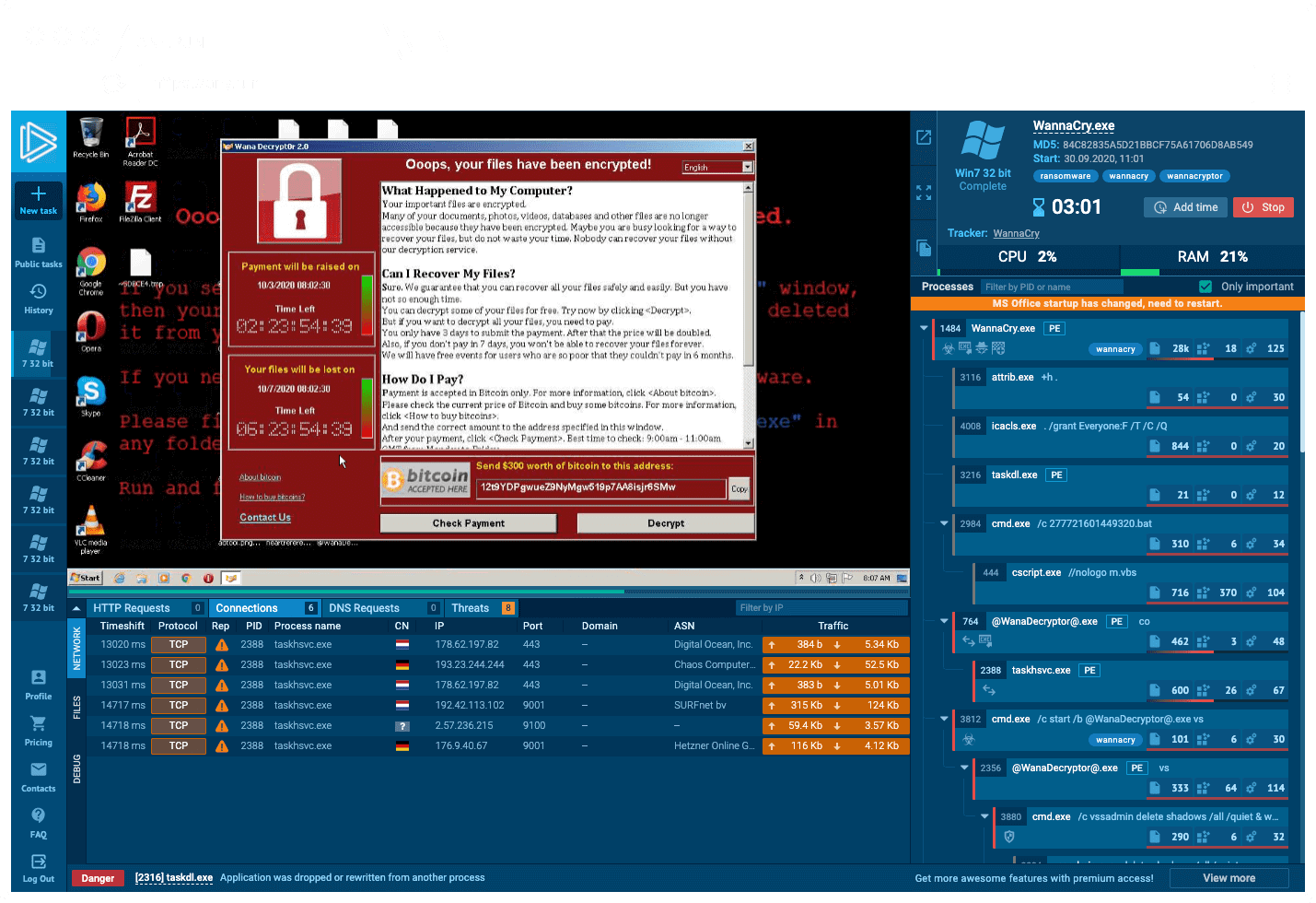
Interactive Online Malware Sandbox
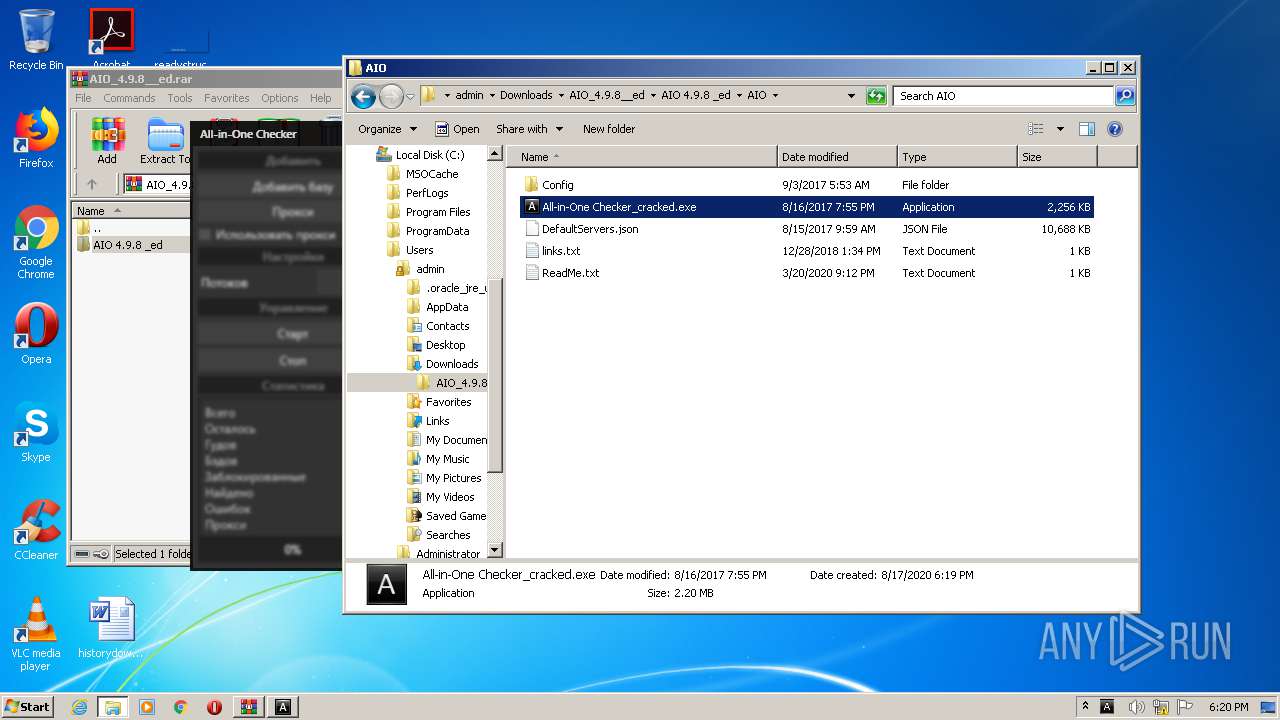
Malware analysis AIO_4.9.8__ed.rar Malicious activity

Routers Roasting on an Open Firewall: the KV-botnet Investigation - Lumen
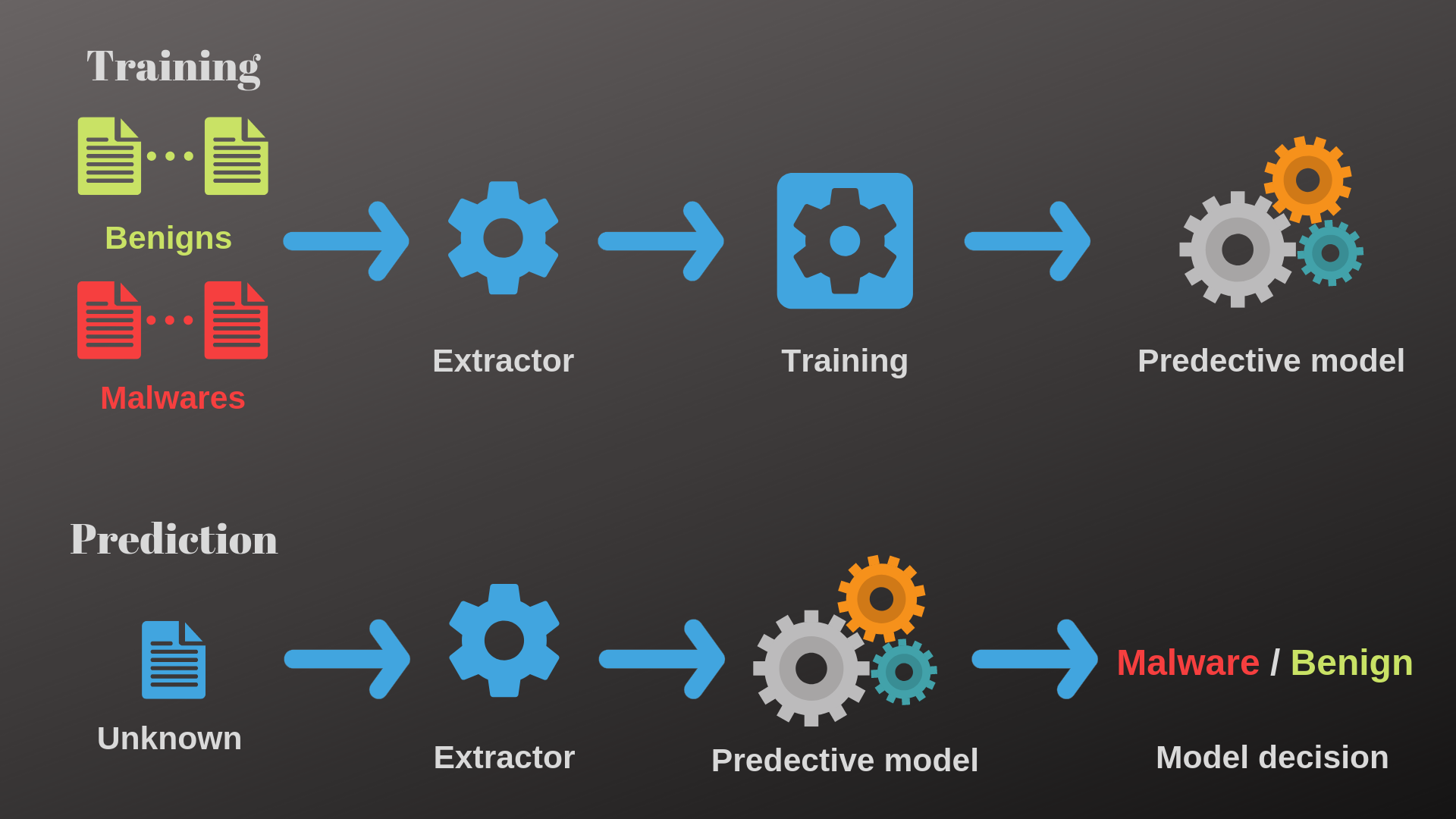
Feature Extraction and Detection of Malwares Using Machine Learning

Routers Roasting on an Open Firewall: the KV-botnet Investigation - Lumen

Malware Analysis: Steps & Examples - CrowdStrike

MetaDefender Cloud Advanced threat prevention and detection

Interactive Online Malware Sandbox

What is Malware? Definition, Types, Prevention - TechTarget
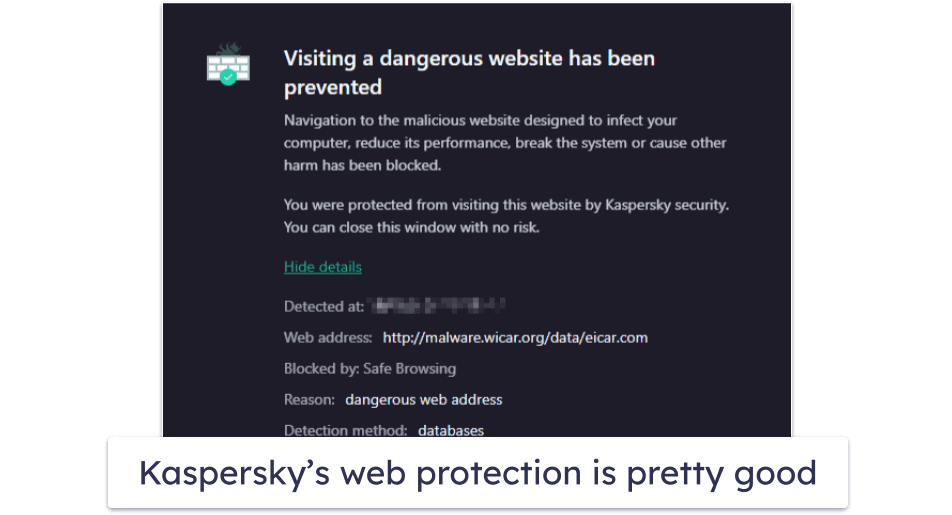
10 Best Antivirus Software in 2023: Windows, Android, iOS, Mac
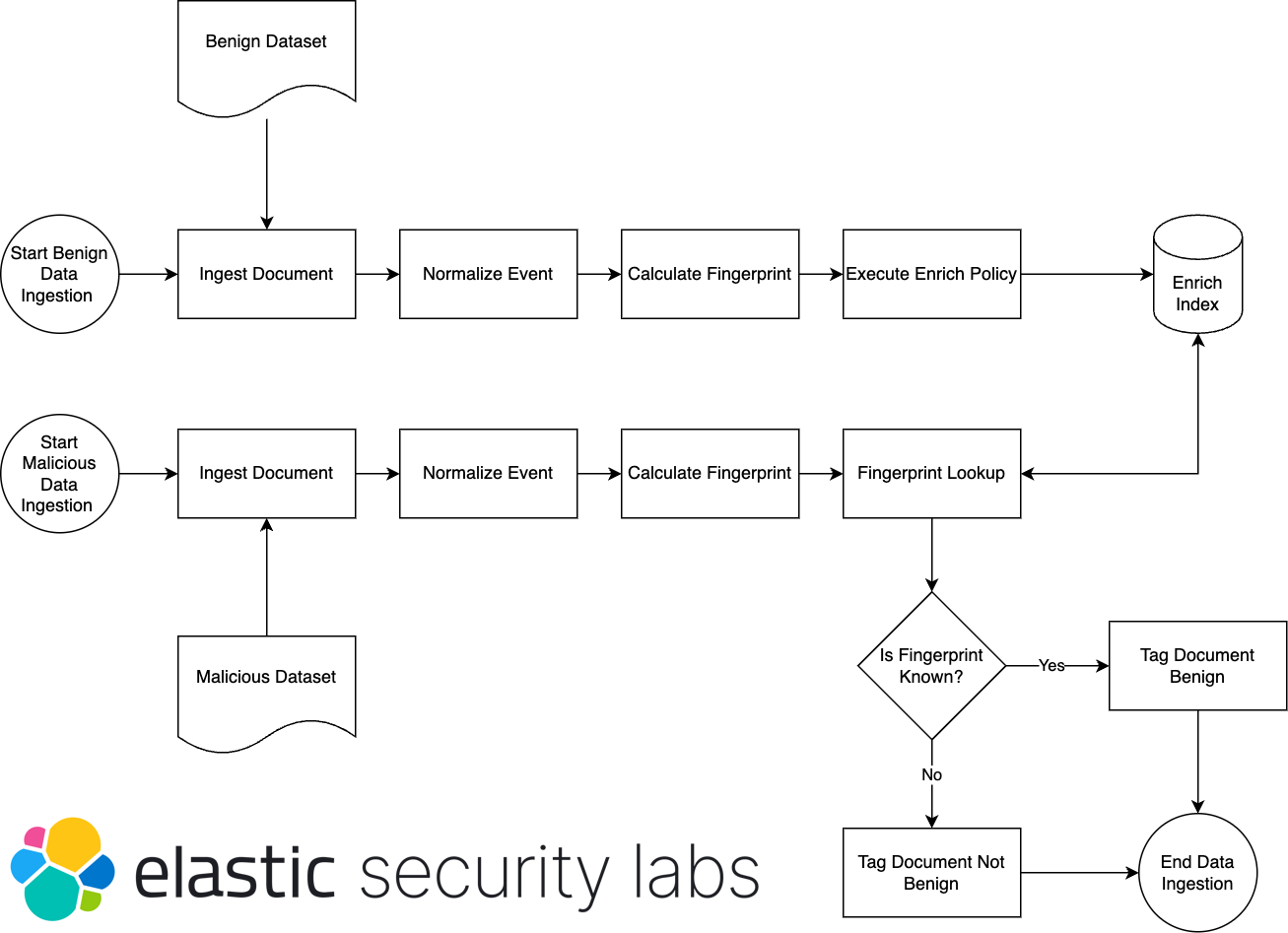
An Elastic approach to large-scale dynamic malware analysis — Elastic Security Labs

The Guide to Ransomware Solutions in 2023 - Security Boulevard
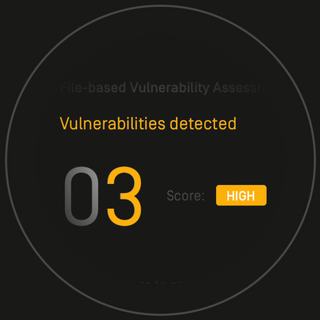
MetaDefender Cloud Advanced threat prevention and detection

Brute Force Attacks: Password Protection
de
por adulto (o preço varia de acordo com o tamanho do grupo)